What is LDAP?
LDAP is the Lightweight Directory Access Protocol, and is a protocol used to access “Directory Servers”. The Directory is a special kind of database that holds information in a tree structure.
The concept is similar to your hard disk directory structure, except that in this context, the root directory is “The world” and the first level subdirectories are “countries”. Lower levels of the directory structure contain entries for companies, organisations or places, while yet lower still we find directory entries for people, and perhaps equipment or documents.
LDAP usage in PHP
We will focus on two LDAP PHP functions which are involved in the CVE, ldap_bind and ldap_errno.
Let’s start with an example of ldap_bind:
1 |
|
The ldap_bind function, as the name suggests, just bind to the LDAP server by providing the LDAP link identifier, an rdn and a password, if the bind is successful the function returns true, else returns false.
Now let’s see another example of ldap_errno.
1 |
|
Basically, the ldap_errno function returns the error number of the last LDAP command, in this case 87 since there is a filter error.
Where is the bug?
Well, there is no evidence of bug or logical errors since there, so let’s create a local environment with slapd LDAP server and phpLDAPadmin, then write a simple PHP page.
1 |
|
The script connects to the local LDAP server and then executes three different bind, the first one with a wrong password, the second one with the correct password but with the last one we pass an array as password argument. Curious about the results? Just take a look.
1 | Bind 1 |
Wow, this is very strange, right? Let’s analyze what happened. Accordlying with official LDAP return codes, in the first bind we received code 49 because the authentication failed, on the second one we received code 0 because the authentication was successful and on the last one we got the same behaviour as the previous scenario but we sent an array containing the string “a”, so we just “logged in” successfully to the LDAP server without knowing the password!
How can this be possible? Well, if you pay attention to the ldap_errno description, you will notice that the return value is about the LAST LDAP command, so if we first bind successfully to the LDAP server and then we bind again passing an array as password argument in the ldap_bind function, something breaks in the PHP function, the bind will not be executed and ldap_errno returns the previous code, which is 0 in this case (LDAP_SUCCESS).
Exploit the bug
How can this bug be exploited in a real scenario? There is a CVE-2018-12421 which says that “LTB (aka LDAP Tool Box) Self Service Password before 1.3 allows a change to a user password (without knowing the old password) via a crafted POST request, because the ldap_bind return value is mishandled and the PHP data type is not constrained to be a string.”
Unfortunatelly there were no Proof of Concept code, so I started analyzing the source code on Github and I deployed the application on my local environment, also I created two users on the local LDAP server.
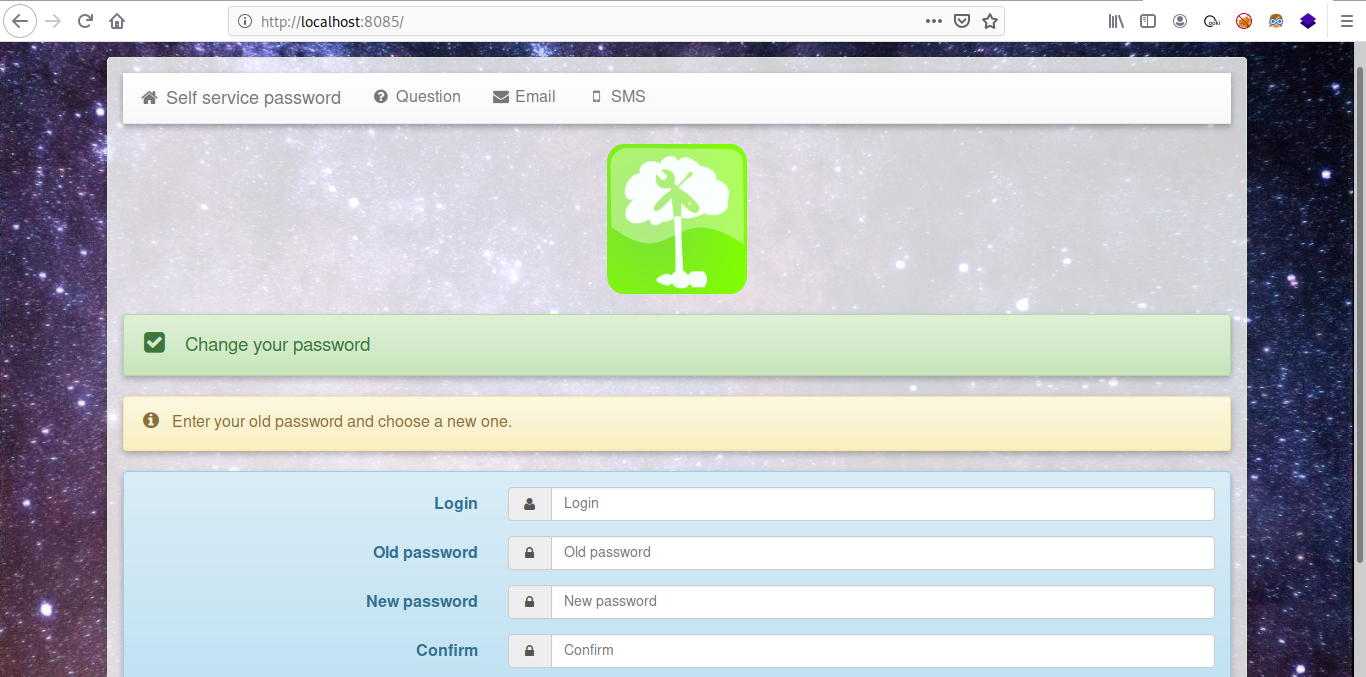
Looking at the source code of “Self Service Passord” change.php file, notice that when an user wants to change his password the following PHP code is executed:
1 | # Bind with old password |
Do you notice something strange? There is no check on ldap_bind return value but only on ldap_errno return code, so we can exploit the vulnerability as described before.
Let’s try to reset the user1 password, fill the form with a random string on old password field and set a new password, then intercept the POST request with Burpsuite and rename oldpassword parameter in oldpassword[].
1 | POST / HTTP/1.1 |
Yes, it happened!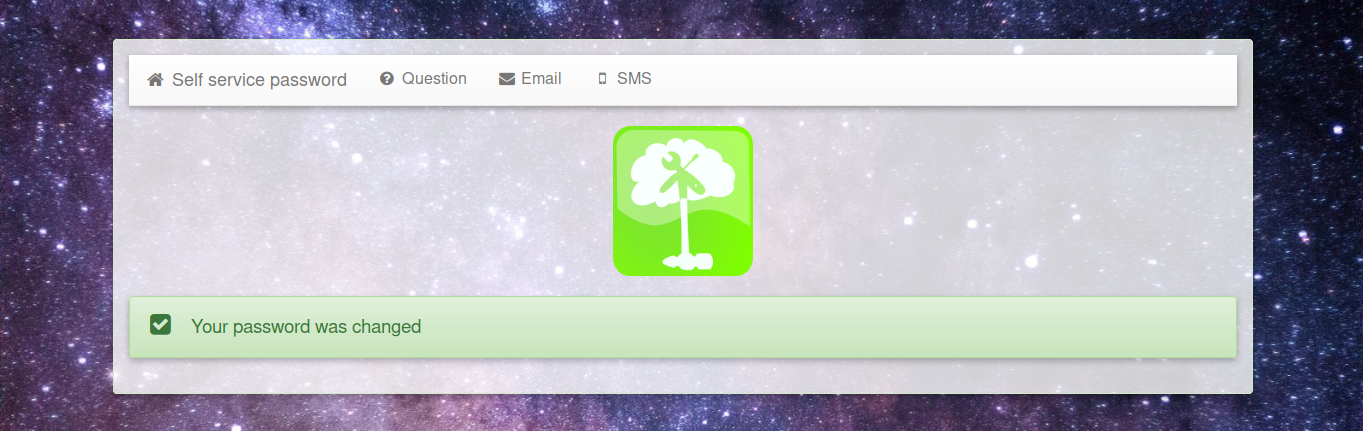
Check on phpLDAPadmin if the password was correctly resetted.
Conclusion
There are a lot of softwares which check only ldap_errno return code without see if the bind is correctly executed.
There is one last question left: how did they fix the vulnerability? Well, they just check the return code of ldap_bind now.
1 | if ( !$bind ) { |